When Your Infrastructure Becomes Their Profit Center
Your applications slow to a crawl, energy bills skyrocket, while cybercriminals silently mine cryptocurrency using your computing power.

Mining Software Attack Sequence
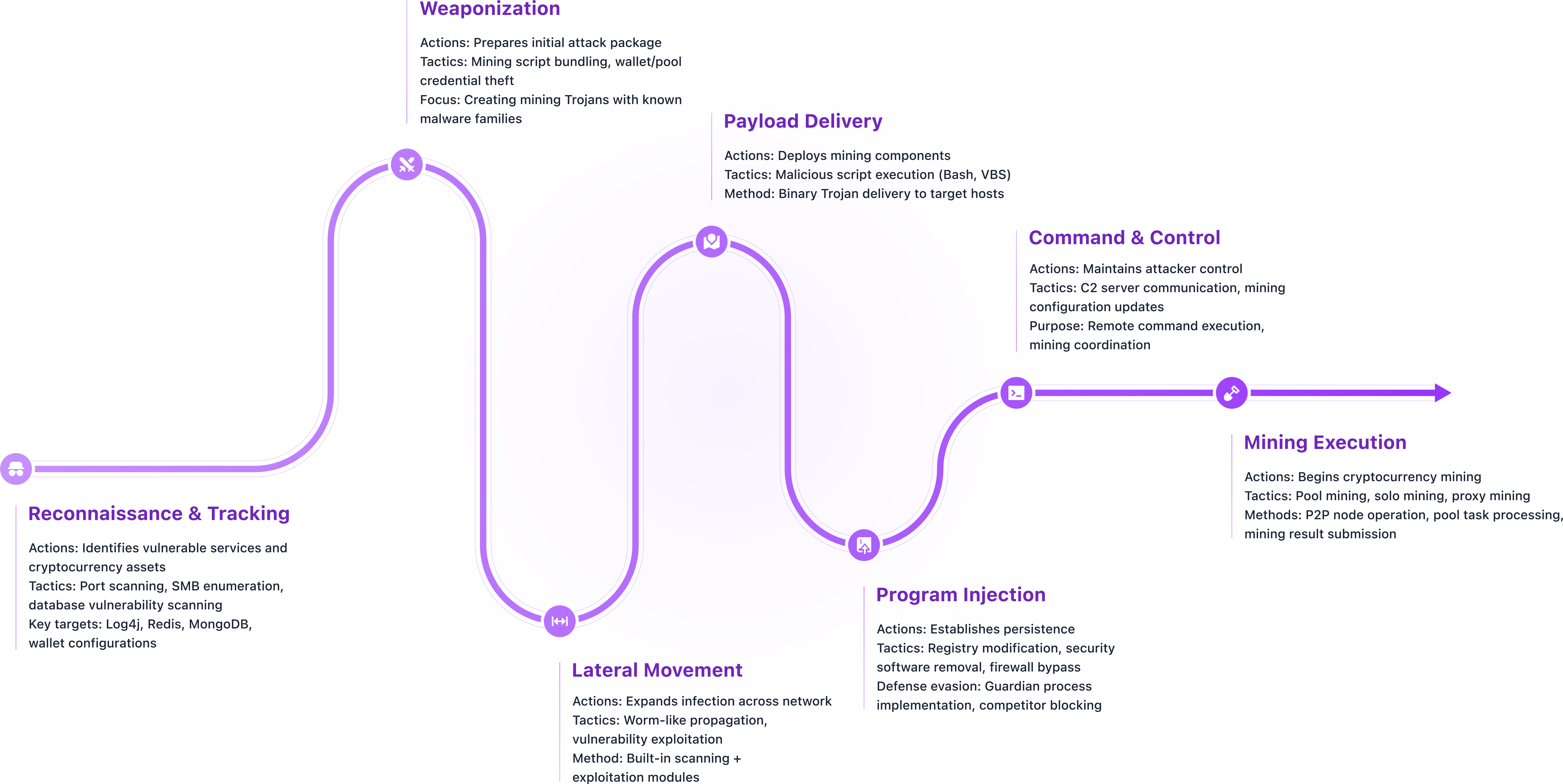
We simulate cryptojacking attacks to expose vulnerabilities and test detection capabilities across 600+ attack variants.

Expose the Silent Threat Before It Strikes
Mining malware operates in the shadows. Most organizations discover it only after months of hidden operation and massive resource drain.
We help you validate your defenses against these stealthy threats before they can establish their profit centers.
Master the Complete Attack Chain
While mining operations distract your team and drain resources, attackers quietly establish deeper footholds for system takeover and data theft.
Our validation platform tests against 600+ attack variants, helping you identify and eliminate vulnerabilities across the entire attack lifecycle before a minor breach becomes a major compromise.


Transform Detection into Predictive Defense
Traditional security measures often miss mining malware because it uses legitimate-looking processes and adapts to evade detection. Our validation platform helps you: