
Enterprise-Grade Validation Framework
Distribute and orchestrate cybersecurity validation across your entire environment while ensuring zero business impact.
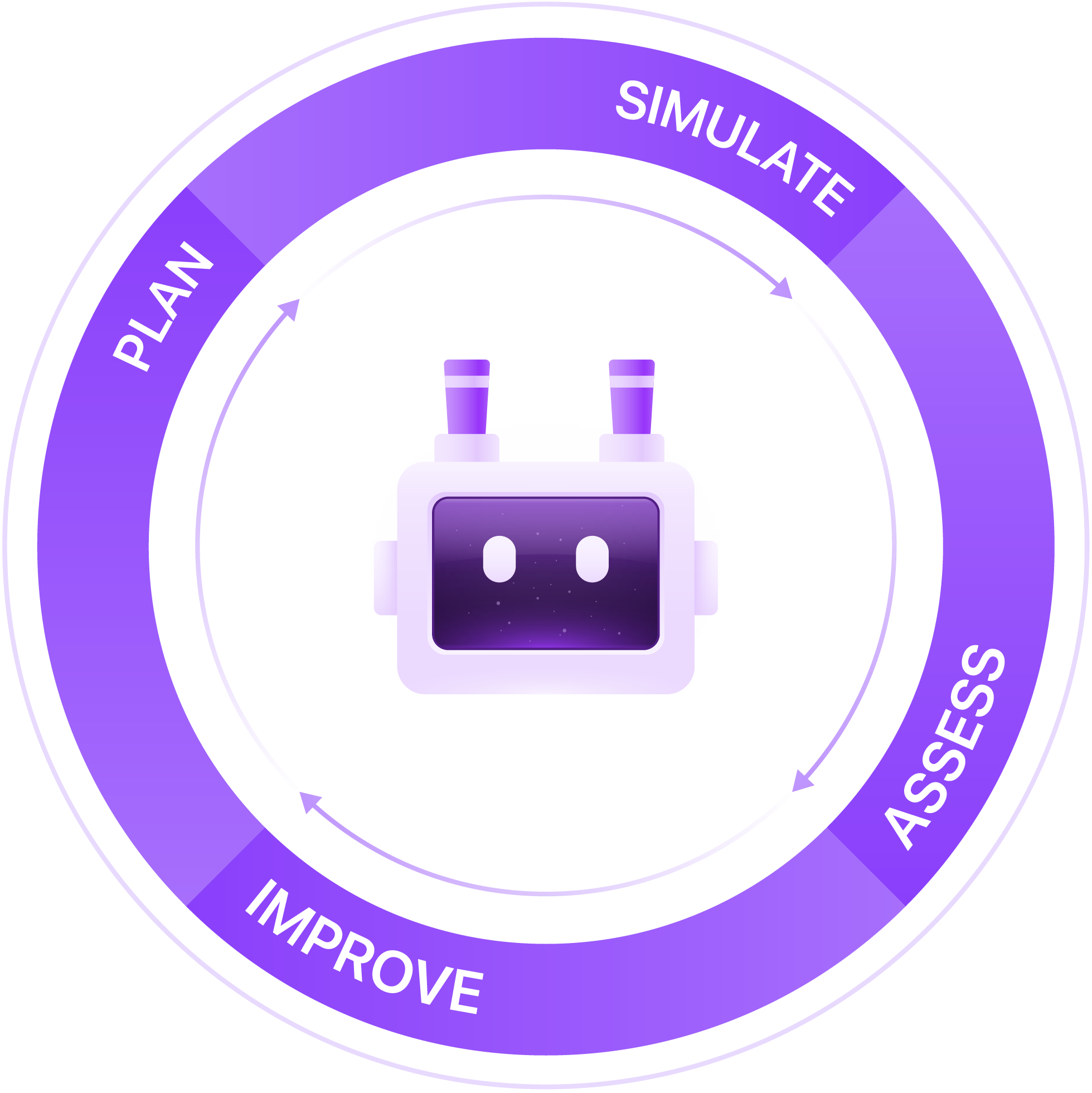
Your Continuous Cybersecurity Validation Journey
Real-World Advanced Persistent Threat (APT) Simulation
Leverage advanced AI to simulate sophisticated cyber threats and attack patterns with comprehensive attack coverage.
Breach and attack simulation mapped to MITRE ATT&CK
AI-driven attack chain orchestration for realistic scenarios
Dynamic scenario adjustment based on your environment
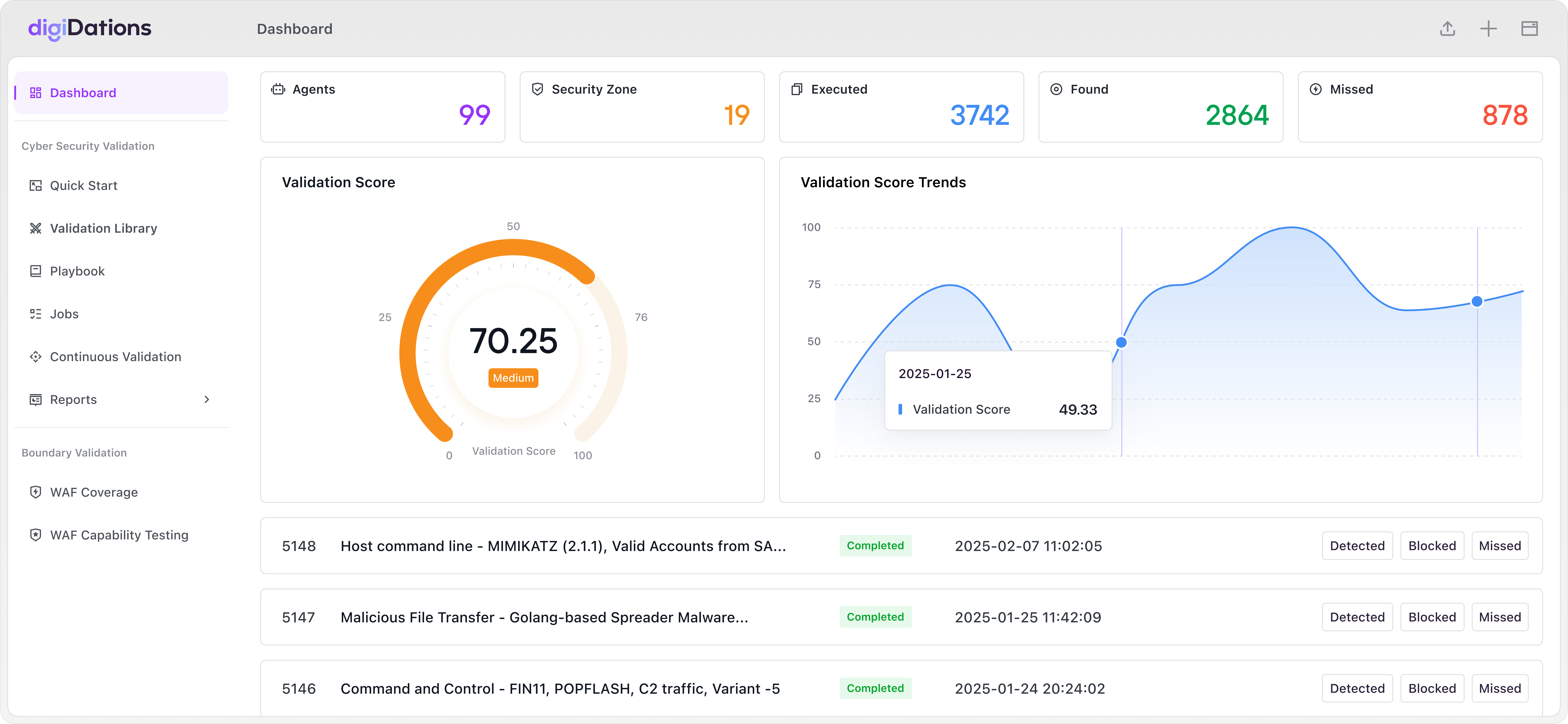
Actionable Security Intelligence & Incident Response
Transform complex security data into clear, actionable insights with comprehensive analytics and reporting.
Multi-dimensional security metrics and KPIs
Customizable executive dashboards and reports
Trend analysis and predictive insights
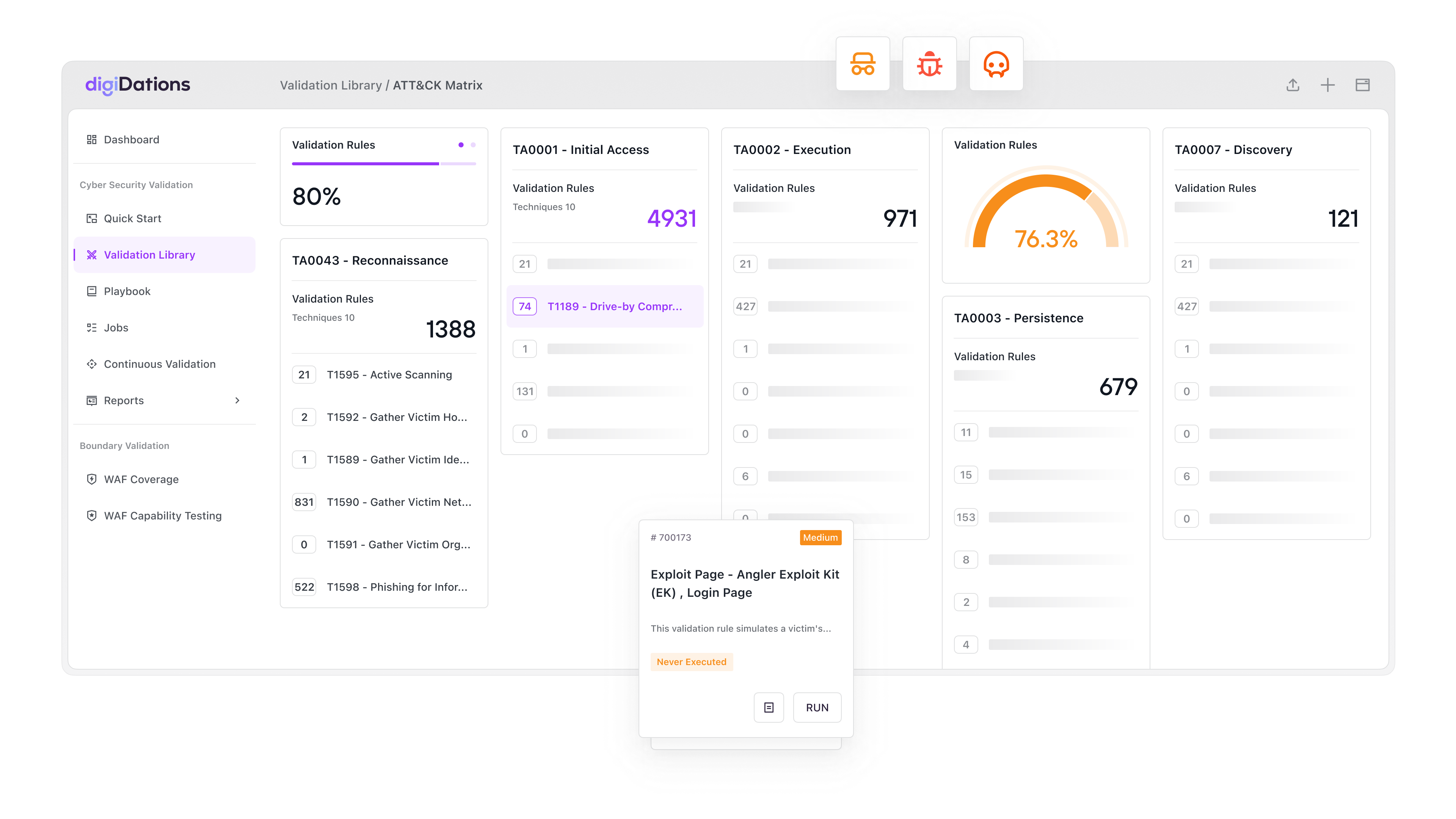
Instant Cybersecurity Validation With Powerful Attack Library
At Your Fingertips
Comprehensive Attack & Threat Intelligence Coverage

Industry-specific Scenarios
Banking & Finance
Healthcare
Energy
Government
……
Common Attack Scenarios
Ransomware
Mining software
Supply chain attack
OWASP top 10
APT groups
Critical vulnerability
……
Security Controls
Email
DLP
NGFW
WAF
Endpoint (Host)
Network Forensics
DNS
IDS / IPS
SIEM
……
From Assumptions to Measurable Security Through Adversarial Exposure Validation (AEV)

On-Premise
Complete control and data sovereignty

SaaS Platform
Quick start with zero infrastructure
Deploy Your Way
Ready to Move Beyond Assumptions?
Start validating your security controls with real-world attack scenarios