What is Security Validation?
Security Validation is the ongoing process of rigorously testing and verifying that an organization’s security tools, configurations, processes, and personnel are performing as intended to prevent, detect, and respond to cyber threats.
Gartner underscores the shift towards solutions that provide consistent, automated evidence of attack feasibility.
At digiDations, we see Security Validation as fundamental to a robust, adaptive, and demonstrably effective security strategy. Our AI-powered validation platform, ATLAS, is engineered to provide this continuous assurance.
Demonstrating True Effectiveness
Cultivating Verifiable Confidence
Enabling Proactive
Defense
Optimizing Security Resources
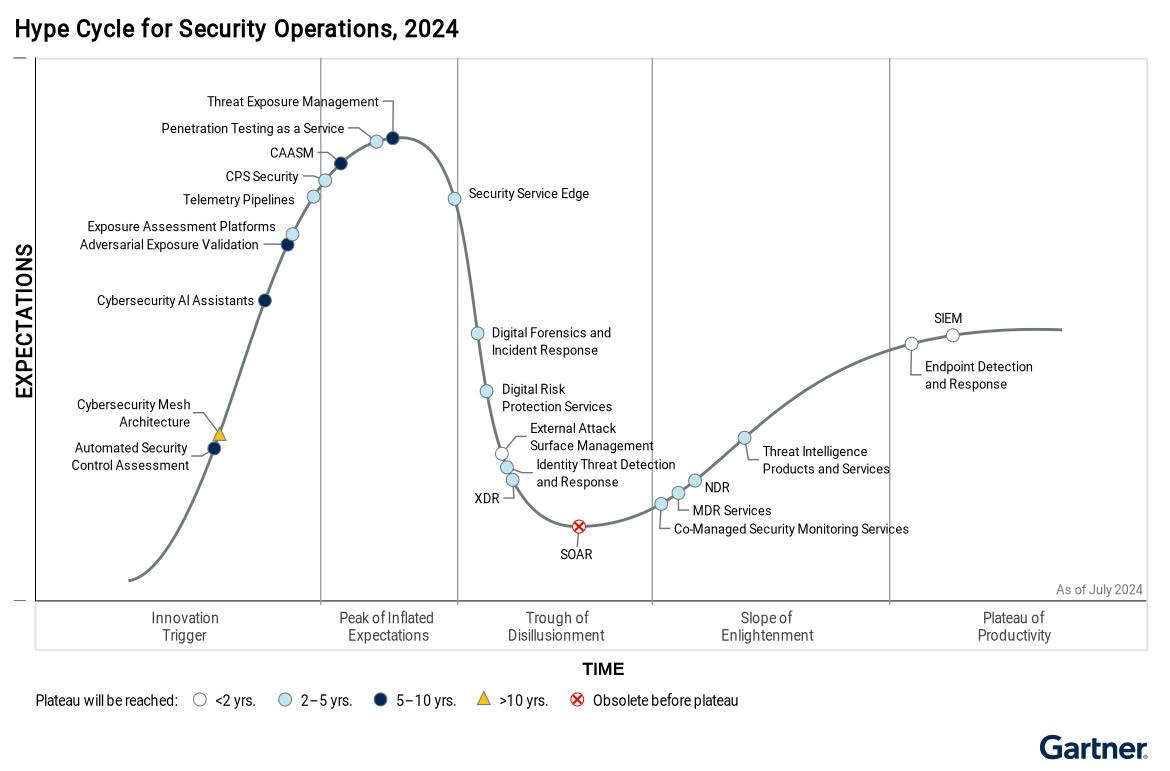
The Evolution: From BAS to AEV
Breach and Attack Simulation (BAS)
BAS solutions helped simulate common attack techniques to test the effectiveness of security controls like firewalls, EDR, and email security.
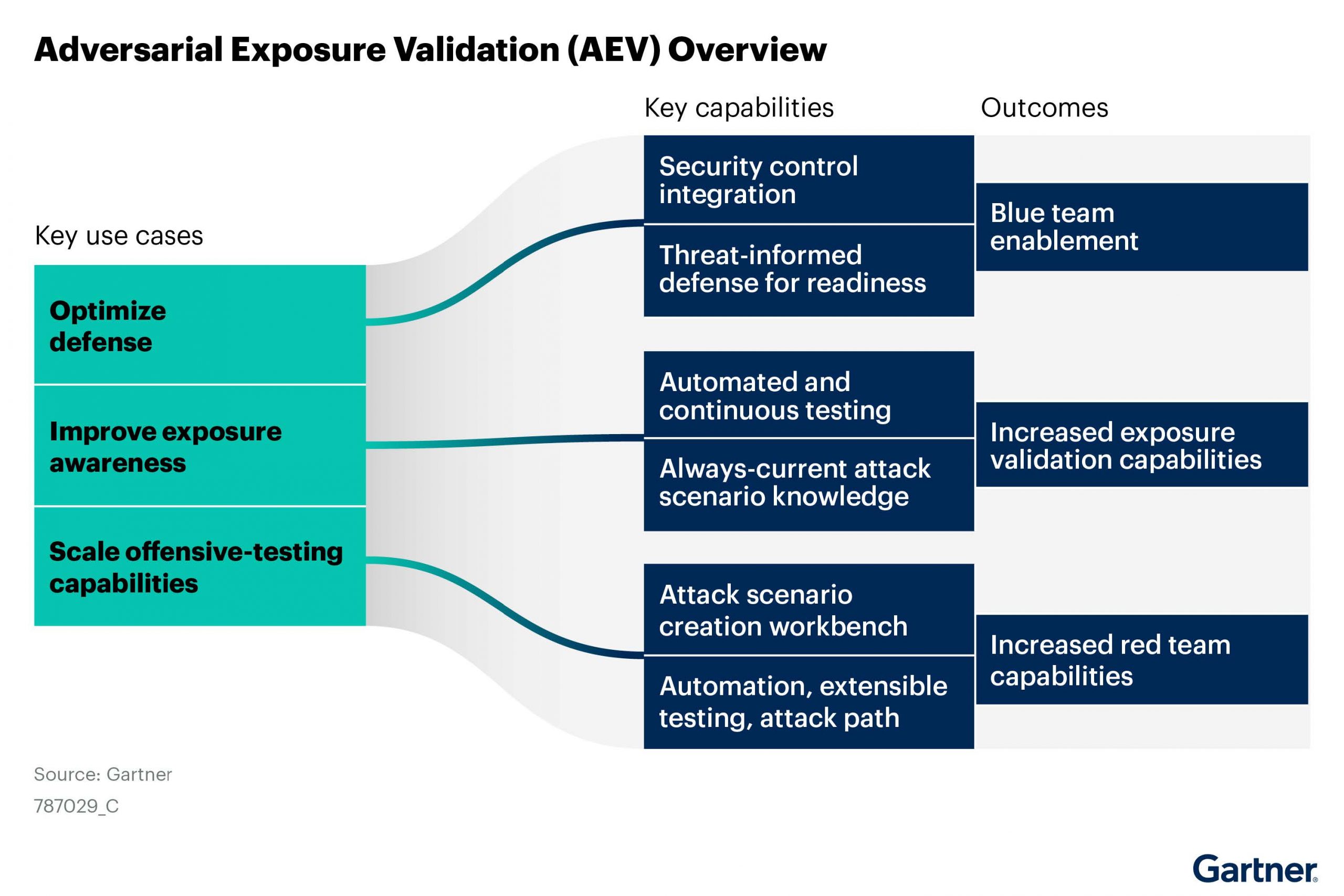
Adversarial Exposure Validation (AEV)
Gartner now uses the term Adversarial Exposure Validation (AEV) to describe technologies that deliver consistent, continuous, and automated evidence of the feasibility of an attack.
Gartner states AEV replaces BAS and automated penetration testing/red teaming technology in their market categorization.
Why the Evolution?
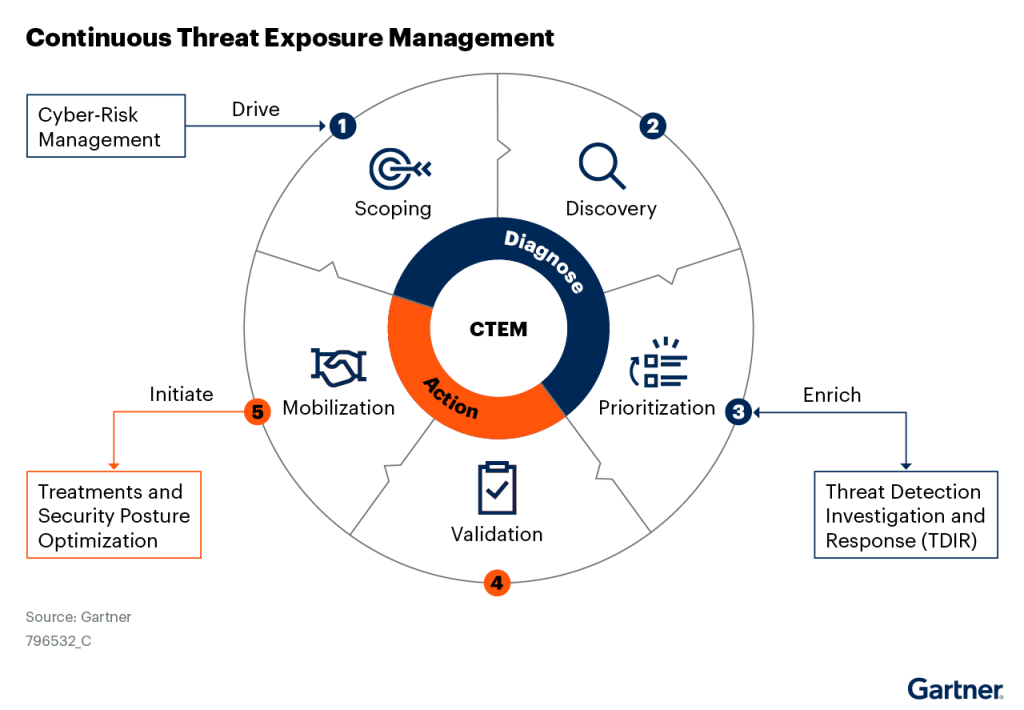
AEV solutions encompass a wider range of validation techniques and outcomes. They focus not just on individual control testing but on understanding the broader exposure landscape, validating entire attack paths, and integrating more deeply into an organization’s overall risk management and Continuous Threat Exposure Management (CTEM) programs.
Key Frameworks Shaping Modern Validation:
Adopting Industry Best Practices