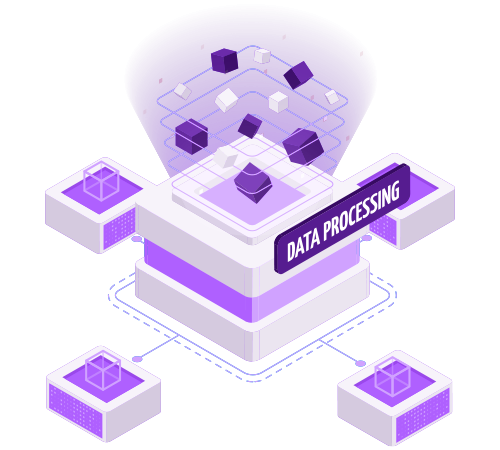
In today’s complex security landscape, organizations often assume their security deployments are functioning as designed. However, critical gaps can emerge:
Our Approach
Drawing from years of security expertise, we’ve developed a comprehensive validation methodology to ensure your security infrastructure operates as intended. Through daily automated validation checks, we verify that every component of your security stack performs optimally.
Validate your security configurations and baseline controls
Network security infrastructure (NGFW, IPS, WAF)

Endpoint security solutions
Email security gateways
Container security systems
Data loss prevention (DLP) tools

Deception technologies (Honeypots)
Application security controls

OT/ICS security systems
Key Benefits

Real Case
A large manufacturing enterprise deployed multiple security products including NGFW, honeypots, and endpoint EDR.
Stage One validation revealed critical gaps:
Post-implementation results:
Start your validation journey today.

Modern enterprises face increasingly sophisticated threats while struggling to:
Our Approach
DigiDations summarizes essential protective functions for security devices. By weekly executing various recent attack actions, it validates detection modules across different security areas and uses a quantitative scoring system for capability assessment. This helps users understand the defense capabilities of security products against various attacks and take appropriate mitigation measures.
Validate how effective are your security products

Network security infrastructure (NGFW, IPS, WAF)

Endpoint security solutions

Email security gateways

Container security systems

Data loss prevention (DLP) tools

Deception technologies (Honeypots)

Application security controls

OT/ICS security systems
Key Benefits

Real Case
A financial institution’s security team questioned their defense effectiveness after experiencing phishing and zero-day breach incidents.
Our validation revealed:
Post-implementation results:
Measure your security effectiveness against real-world threats now.

Organizations with mature SIEM/SOC platforms face increasingly complex challenges in threat detection and analysis:
Our Approach
DigiDations collects attack techniques from threat organizations and organizes them into scenarios using the kill chain or MITRE ATT&CK framework. It systematically validates the correlation analysis and threat hunting capabilities of SIEM/SOC platforms, allowing users to create more rules that improve alert accuracy and reduce alert fatigue.

Key Benefits

Real Case
A major internet company invested significantly in its SIEM platform but struggled to identify genuine threats amid millions of daily security logs, especially after an internal data breach.
Our validation revealed:
Post-implementation results:
Turn your security operations center into a proactive defense powerhouse now.

Even with established security operations, organizations face critical challenges in incident response:
Our Approach
DigiDations collects various attack techniques from threat organizations and organizes them into scenarios, regularly conducting purple team exercises to execute these threat scenarios. Atlas will integrate with internal ticketing systems to track the status of ticket workflows and will use logs to understand response and handling results. This helps users validate the complete process from alert detection to ticket resolution, assess operational efficiency, and evaluate MTTR.

Key Benefits

Real Case
A technology company with a mature security team faced challenges in incident response efficiency. Initial response times exceeded 30 minutes, with resolution taking over an hour.